Audit Process Tracking
 |
Windows 10
To access, do the following
-
Expand Local Policies
|
|
-
Expand Audit Policy
|
|
-
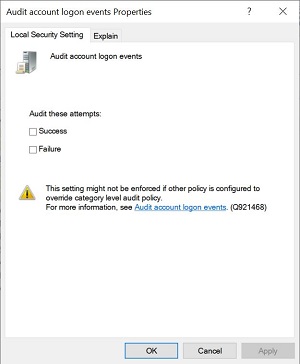
Double-click Audit account logon events
|
|
 |
Audit account logon events
This security setting determines whether the OS audits each time
this computer validates an account’s credentials.
Account logon events are generated whenever a computer validates the
credentials of an account for which it is authoritative. Domain
members and non-domain-joined machines are authoritative for their
local accounts; domain controllers are all authoritative for
accounts in the domain. Credential validation may be in support of a
local logon, or, in the case of an Active Directory domain account
on a domain controller, may be in support of a logon to another
computer. Credential validation is stateless so there is no
corresponding logoff event for account logon events.
If this policy setting is defined, the administrator can specify
whether to audit only successes, only failures, both successes and
failures, or to not audit these events at all (i.e. neither
successes nor failures).
Default values on Client editions:
Credential Validation: No Auditing
Kerberos Service Ticket Operations: No Auditing
Other Account Logon Events: No Auditing
Kerberos Authentication Service: No Auditing
Default values on Server editions:
Credential Validation: Success
Kerberos Service Ticket Operations: Success
Other Account Logon Events: No Auditing
Kerberos Authentication Service: Success
Important: For more control over auditing policies, use the settings
in the Advanced Audit Policy Configuration node. For more
information about Advanced Audit Policy Configuration, see https://go.microsoft.com/fwlink/?LinkId=140969.
